As technology improves for everyday users, so does the technology available to hackers and cybersecurity attackers. Many businesses have implemented technical tools to protect their employees and operations from threats in the ever-evolving technological landscape. And while hackers can meet, beat or exceed some of these tools, they’ve discovered it can be time consuming and cost prohibitive. Many hackers have since shifted their approach to an old school attack method: email. Crafting this type of attack is fast, cheap, and easy as it requires limited skills and equipment. It is also much harder for businesses to protect against, forcing them to depend on their employees as the last line of defense.
Business email compromise
One popular approach to using email as an attack is through business email compromise. Also referred to as a BEC scam or email account compromise, it is used by hackers to trick victims into sending a sum of money (sometimes gift cards) or personal information about the organization or an employee (think: passwords, social security numbers, etc.). Usually, the BEC email will appear to come from a company CEO or another high-level employee within the organization. The hacker will request money or another form of payment such as a gift card from the unsuspecting victim of the BEC scam. This hacker is generally a single person or a small group who can find basic information about an organization from a quick internet search to craft an accurate impersonation of someone well known at the organization. They then create an email address similar to one used by the organization to fool their target into sending money to the wrong address.
To prevent BEC, performing a thorough email analysis is crucial. Checking if the email is coming from the exact email address of the requesting party is an easy step that can save an organization from being hacked for hundreds or thousands of dollars. A trick that BEC scammers use is to create an email address that is one or two characters different from the legitimate email address. For example, johndoe@business.net could be changed to john.doe@business.net to trick a victim.
After verifying the email address, it’s best practice to verify payment requests in person or over the phone, if possible. Being cautious with sharing company information online is key to preventing elaborate BEC scams from the start.

GCI’s remote-first workforce sets the standard for large employers around the nation
Read the blog
Phishing with links
There are many types of phishing attacks where emails are sent to get a user to complete an action. Typically, this involves clicking an external link within the email. It will then route the user to a website that looks nearly identical to the website they’re expecting. This website will ask for information like a password, credit card information, or a bank PIN.
To protect from phishing scams, avoid directly clicking on links within an email. Instead, try opening a new webpage and using a search engine to research the website. Avoid signing into accounts via links in an email.
Phishing with attachments
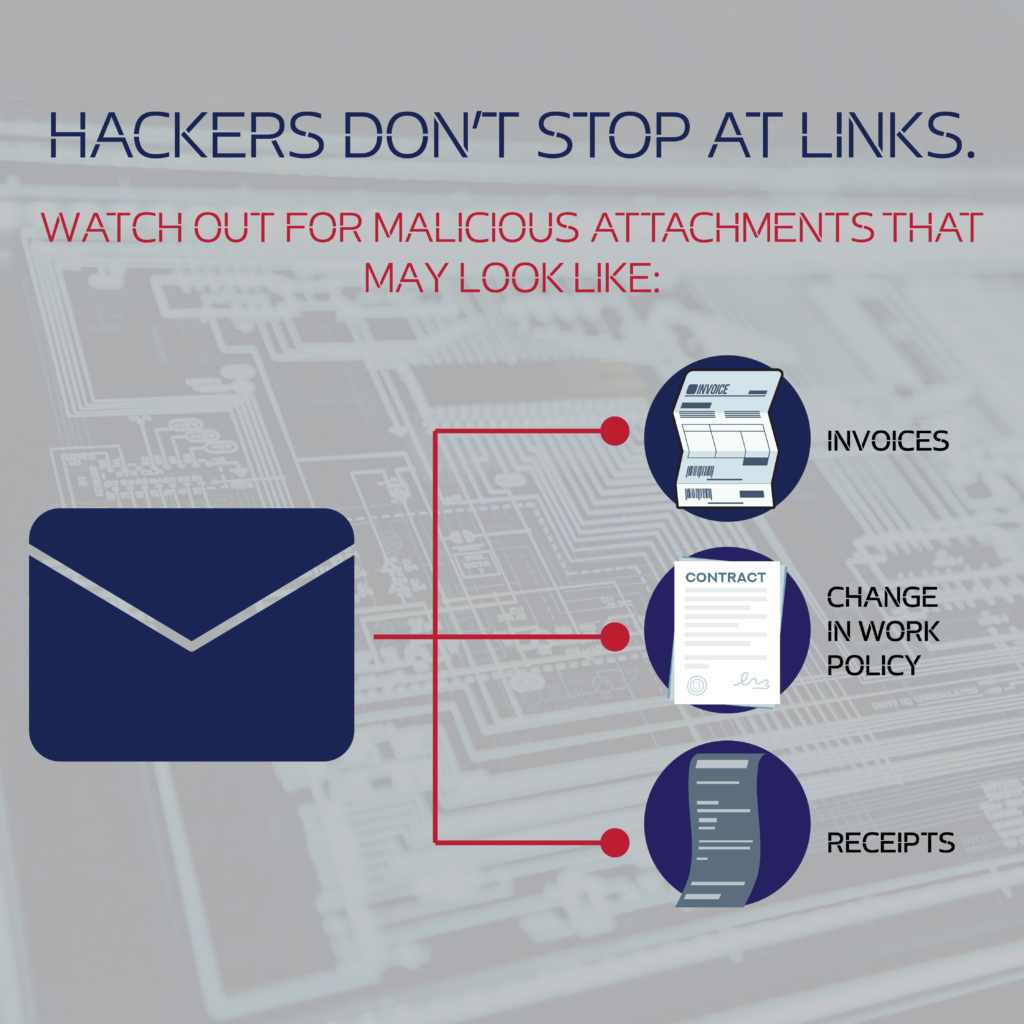
Hackers don’t just stop at links, they also include malicious attachments, usually labeled in a way to get the user’s attention. Claiming to be invoices, receipts, or changes in work policy, these types of attachments have compromised many businesses.
Some email providers offer additional scanning services for these types of attachments, where the attachment is opened within a safe environment and then sent on to the user if deemed secure. It is also best practice to remind employees to consider if they were expecting an attachment before opening it, especially from an unknown sender.
How to protect yourself and your employees
Preventative care techniques include ensuring everyone in the workplace is frequently backing up their information to ensure it is not being skimmed by phishers, enforcing strong password policies, and using multi-factor authentication services that warn users when phishing threats are detected.
More information on phishing and BEC prevention for businesses can be found from the Federal Trade Commission. Federal Trade Commission tips include cloud backups and WPA2 encryption which protect vulnerable personal information by storing it on a separate service. Suspected phishing and BEC should be reported to FTC.gov/complaint, spam@uce.gov, and reportphishing@apwg.org. These organizations will investigate phishing or BEC schemes at the source to stop and prevent future victims.
If you want to learn even more about how to protect your business, check out the on-demand video webinar from Alaska Small Business Development Center hosted by Peter House, Deeptree CEO. The webinar provides professionals with the knowledge of cybersecurity access and information technology concepts.